Information exposure
CWE-200: Exposure of Sensitive Information to an Unauthorized Actor
About
As the name suggests, information exposure vulnerability refers to the exposure of sensitive information to an actor that is not explicitly authorized to have access to that information. Consequences resulting from it can vary from minor to severe, depending on the type of information that is exposed.
Attack
We are going to observe the header of the response of the server.
- Use the following curl command to send a request to the server.
curl -I http://localhost:5000/healthFor sending the request, you can also use Postman, but the aim of this is also to show you how to use curl. Curl is a command-line tool included in most operating systems that allows sending HTTP requests and viewing responses in the terminal. If you prefer GUI applications, you can use Postman.
- You should get a response similar to the following:
HTTP/1.1 200 OK
X-Powered-By: Express
Access-Control-Allow-Origin: *
Content-Type: application/json; charset=utf-8
Content-Length: 15
ETag: W/"f-v/Y1JusChTxrQUzPtNAKycooOTA"
Date: Mon, 17 Apr 2023 20:00:08 GMT
Connection: keep-alive
Keep-Alive: timeout=5-
Investigate the response and determine, which information is sensitive and could be used to exploit the application.
-
The information that could potentially be used by an attacker in this request response includes:
- X-Powered-By header: Reveals that the server is powered by Express.js. This information could be used to target known vulnerabilities or weaknesses in the framework or its dependencies.
- Access-Control-Allow-Origin header: Reveals that the server allows requests from all origins. It could potentially allow cross-site scripting (XSS) attacks or other types of attacks that rely on cross-origin requests.
- ... information contained in other headers can also potentially serve as an attack vector.
Security Headers Scanner
We are going to use the Security Headers Scanner (opens in a new tab) to check the security headers of the HackHealt app. It will also give us recommendations on how to improve security.
To use the Security Headers Scanner, we need to make the Express server publicly available. We will use ngrok (opens in a new tab) to expose the local server to the Internet.
- ngrok is already installed in the VM. You can verify by running the following command in the terminal:
ngrok version- Make sure the server is running locally.
- In the command line, run:
ngrok http 5000You should get a response similar to the following:
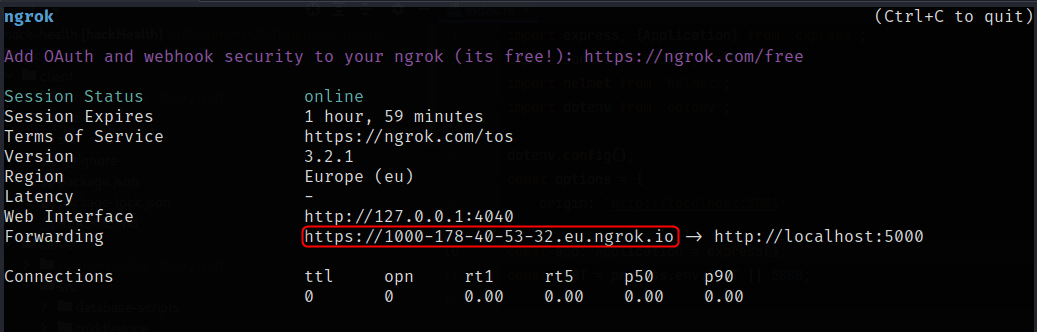
The marked part in Forwarding field contains the URL to publicly access your local server. Kind of like a tunnel to your local server. Magic, right?😄
- Copy the URL from the
Forwardingfield and paste it into the Security Headers Scanner.
At the end of the URL, add /health to check the existing endpoint.
Final URL should look like this: https://<ngrok_string>.ngrok.io/health
- Scan the URL and observe the results.
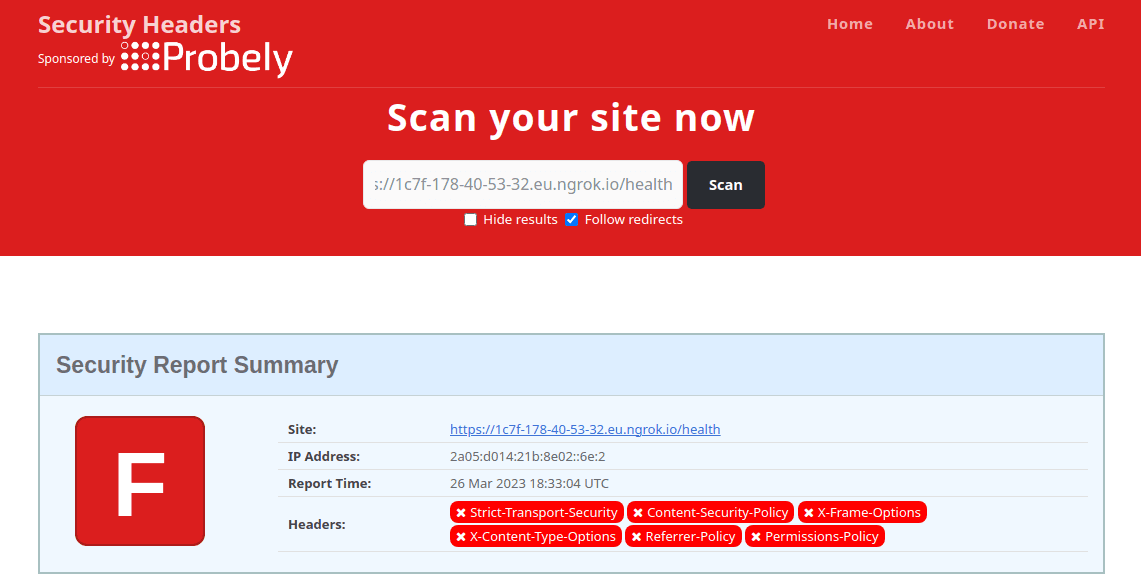
As you can see, the scan reveals that the server is not configured properly. It is missing the most crucial security headers.
Prevention
We are going to use Helmet middleware to prevent information exposure. Helmet automatically sets various HTTP headers and also removes some to comply with web security standards. It is a collection of 14 smaller middleware functions.
- In
index.jsfile, importhelmetmiddleware:
import helmet from "helmet";- Add
helmetmiddleware to the server:
app.use(helmet());- Server is due to nodemon restarting automatically. Try to scan the URL again in the Security Headers Scanner.
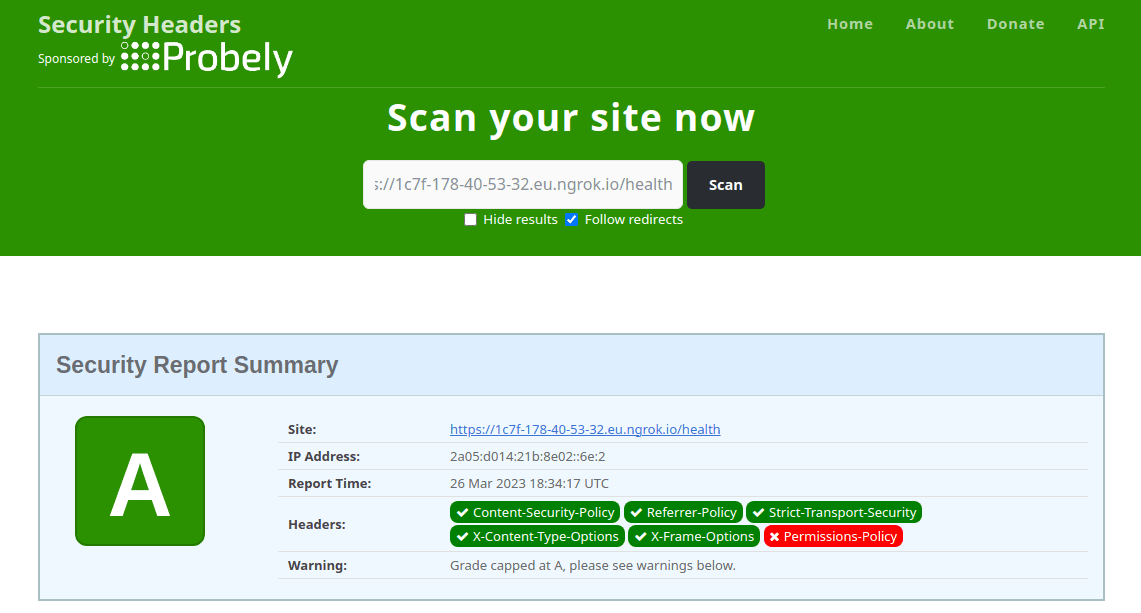
By just adding 2 lines of code, we were able to drastically improve the security of our application.
The helmet sets the header to default values. You can customize the headers by passing options to the middleware. For more information, visit page (opens in a new tab).
Verification
Try running the curl command again to see the response.
curl -I http://localhost:5000/healthAs you can observe, many headers related to security has been added. Also, the X-Powered-By header has been removed, so the attacker can no longer determine which framework is used.